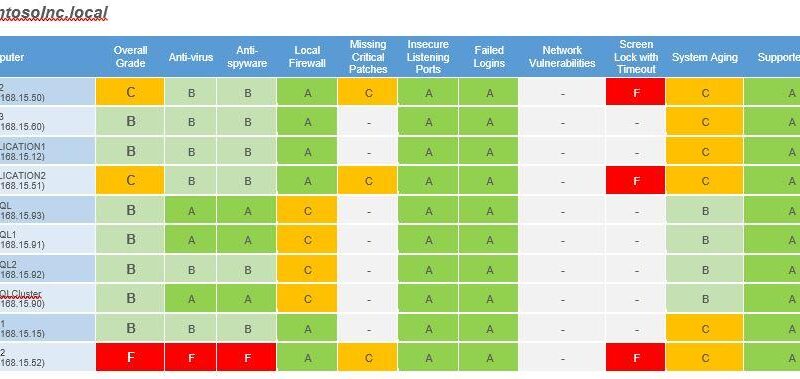
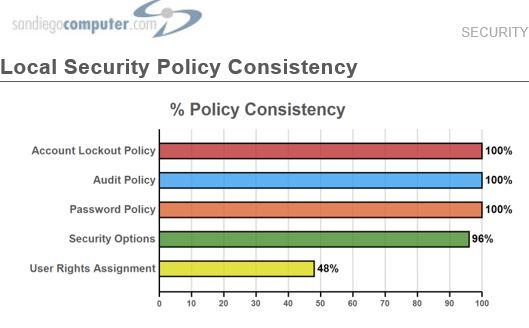
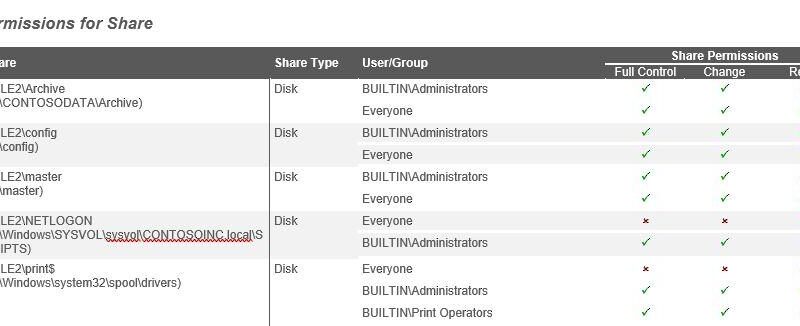
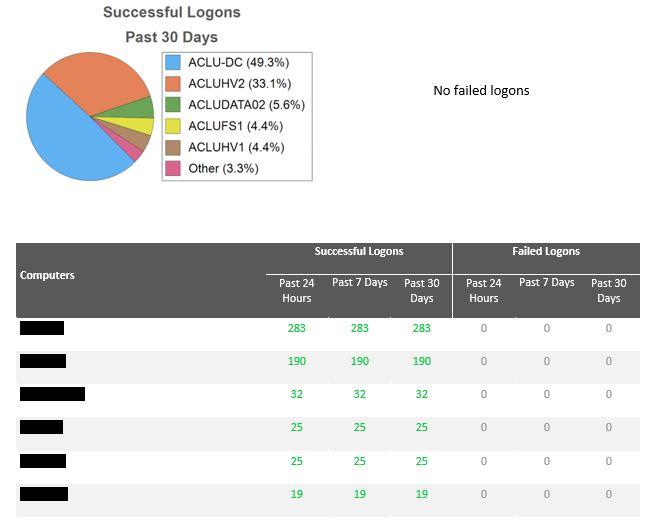
Did you know that San Diego Computer Consulting can do a security assessment report?
We have tools that allow us to look at the security of your network and identify the strengths and weaknesses of your network. In today’s very nefarious world, IT security is one the most important things to pay attention to. Most all theft is done electronically. Making sure your IT network is secure is done through a series of measures. We at San Diego Computer Consulting help guide our clients to use the right firewalls, anti-virus, anti-ransomware, the best email protection and most importantly the best backup solutions.
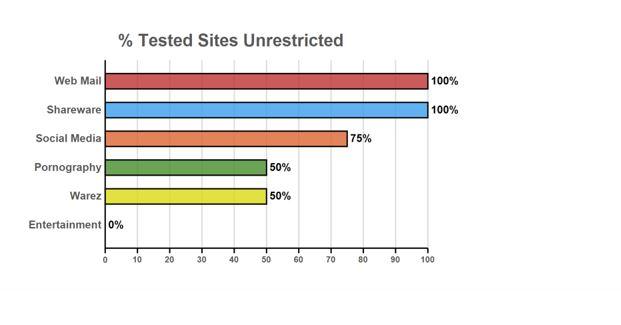
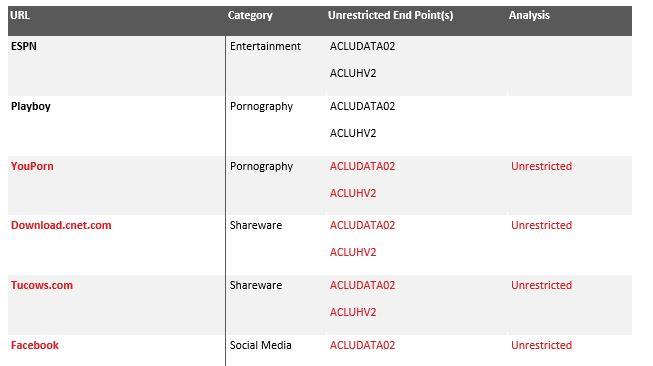
This all starts with us being able to provide a Security Assessment. Though this is not penetration testing, the Security Assessment is an important tool that we use at San Diego Computer Consulting to help determine security deficiencies in a network. This tool also allows us to take a look at your entire network, computer, server, wifi, and other network connections and give us a report on the strengths and weaknesses of the security of those individual devices.